In today's digital age, businesses rely heavily on mobile applications to streamline their operations, increase efficiency, and ultimately, drive profits. With the rise of iOS devices in the business world, it has become essential for companies to prioritize the security of their business applications. As a business owner, your top priority is likely to be the success and growth of your company. However, with cyber threats becoming more sophisticated and prevalent, the security of your business data and confidential information is at risk.
In fact, according to a recent study by Verizon, 43% of data breaches involved small businesses. This makes it crucial for businesses to take proactive measures to enhance their iOS app security. By implementing the best practices for iOS app security, you can not only protect your sensitive data but also ensure the smooth functioning of your business operations. So let's delve deeper into the importance of revamping your business applications to prioritize iOS app security.
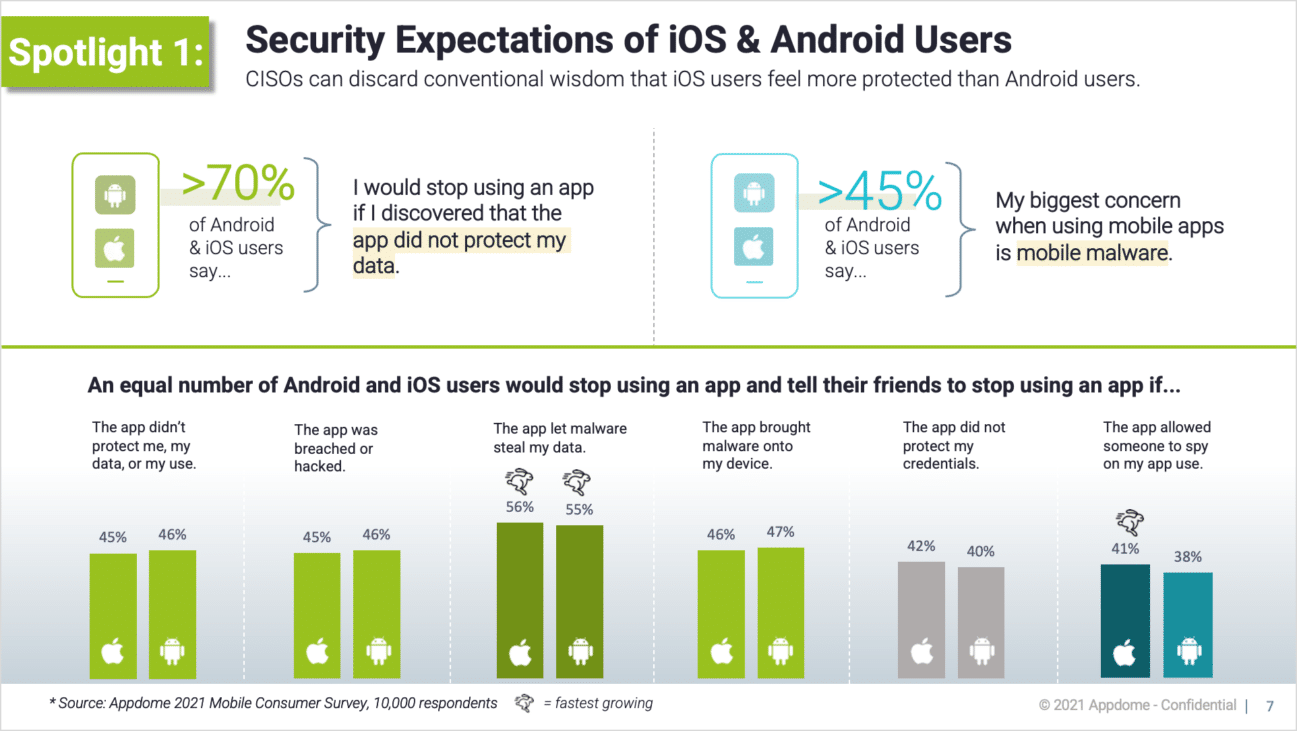
Understanding the Threat Landscape for iOS Applications
The digital terrain of iOS applications is increasingly becoming a battleground where businesses must defend their data against the onslaught of cyber threats. As these applications evolve into essential tools for business operations, their appeal to malicious actors grows exponentially. A staggering statistic reveals that a vast majority of mobile apps, 75% to be precise, do not pass the most basic security tests. This vulnerability opens the floodgates for hackers, who, with sophisticated techniques, can exploit weaknesses to access sensitive information, thereby endangering user privacy and business continuity.
Mobile apps are always at risk of threats. Even though Apple has strong security, cybercriminals are finding new ways to attack iOS apps. They use malware to steal data without users knowing.
They also trick people into giving access through phishing scams. Security breaches not only cause data loss but also damage customer trust, which is hard to regain.
Businesses must update their apps often to stay competitive. But each update might accidentally let in new threats. So, regular security checks are a must.
To stay safe, businesses should first understand the different types of threats. These include hacking, phishing, weak encryption, and software bugs.
Then, they can take steps to prevent attacks. This means having strong security measures. It also means monitoring threats and updating defenses. In short, protecting iOS apps needs constant effort and following best practices.
Protecting Your App with Data Encryption
In the digital world, keeping your app secure is crucial. Data encryption plays a key role in safeguarding sensitive information from cyber threats. It works like a secret code, scrambling your app's data into a puzzle that only authorized users can solve. Using encryption standards like AES and SSL/TLS is like deploying elite guards to protect your app's valuable information.
Data breaches can be costly. A 2020 report by IBM found the average cost of a data breach was a staggering $3.86 million. Strong encryption practices are crucial. Encryption doesn't just hide data; it makes it useless to intruders. Even if unauthorized access occurs, your data remains secure. A study by Cybint Solutions showed that 95% of cybersecurity breaches result from human error.
Implementing encryption is about creating a culture of security. Encrypting data in transit (when moving across the internet) and at rest (when stored) greatly reduces the risk of interception or theft. This dual-layer encryption strategy is essential in today's era of sophisticated and persistent cyber threats.
Many people think encryption is complex. But the main idea is simple: it protects your app's safety and your users' privacy. By prioritizing encryption, businesses can safeguard their digital assets from cyber threats. This ensures their app remains secure for business growth and customer interactions.
Implementing Strong Authentication Mechanisms
In the digital business world, sensitive information is only as secure as the weakest access point. Strong authentication acts like a sophisticated lock and key system to prevent unauthorized access. Multi-Factor authentication (MFA) is an essential shield against cyber intruders.
Traditional passwords alone are not enough. The Verizon Data Breach Investigations Report states 81% of hacking breaches involve stolen or weak passwords. MFA adds extra verification steps beyond just a password. These could include something the user knows (a password), has (a mobile device), or is (biometrics like fingerprints or facial recognition). This multi-step approach significantly reduces unauthorized access risk, even if a password is compromised.
Security is crucial for business apps. Biometric authentication has become popular. It uses physical traits like fingerprints, making it hard to fake. A study found most companies used biometrics in 2020. Combined with other checks, it enhances app security greatly, blocking unauthorized access.
However, strong authentication is about more than just technology choices. It needs a balanced approach considering user experience too. Authentication processes that are overly complex can frustrate users and reduce productivity. So, solutions must be secure yet user-friendly. Businesses can protect digital assets without reducing efficiency by carefully integrating authentication tech. Their defenses stay robust yet accessible to authorized users.
Regular Security Audits and Penetration Testing
For iOS app security, regular audits and penetration tests are vital tactics. Like training drills before battle, they reinforce defenses and expose vulnerabilities before hackers can exploit them. This proactive strategy prepares apps to withstand sophisticated cyberattacks.
Security checks dig deep into the app's design, looking for weak spots. These checks are key to making sure security is strong and right for the business. It's a careful process, as small mistakes can lead to big problems.
Penetration testing, or ethical hacking, works with the audits. Certified experts use real hacker tools and tricks to try to break in. This battle testing shows how well the app's security really works against attacks. A Ponemon Institute study found that companies that test often are much better at finding and fixing weak spots, showing how valuable this method is.
Cyber threats keep changing quickly, with new dangers popping up all the time. That's why regular security audits and penetration tests are a must. The cybersecurity world is always shifting, so defenses have to shift too. Skipping these vital steps is like leaving castle gates wide open for trouble.
Security is key for businesses today. Hackers are always on the lookout for flaws in apps. Putting good practices in place helps find issues before hackers can take advantage of them. This protects the app, users, and the business's reputation.
Secure Coding for iOS Apps
Building secure iOS apps is crucial. A small mistake can give hackers access. The OWASP group says many software issues come from not following secure coding rules. So, iOS developers must know how to write secure code.
One important step is input validation. This checks all data entering the system and blocks anything suspicious. It prevents attacks like SQL injection, which is still a big threat according to Verizon. Output encoding is also vital. It makes data safe before showing it in the browser. This stops cross-site scripting (XSS) attacks. And proper error handling ensures errors don't reveal vulnerabilities to hackers.
Following these steps makes iOS apps much harder to hack. A little care in coding goes a long way in protecting the app and its users. Businesses can't afford security lapses in today's world.
Apple has clear guidelines that developers should follow. These guidelines help make apps secure. They include app sandboxing and code signing. These tools protect apps from the start.
As cyber threats become more complex, secure coding is crucial for iOS apps. It doesn't just defend apps - it actively protects them. Secure coding ensures business apps stay safe in the digital world.
Leveraging Apple's Security Features and Updates
Cybersecurity is always changing. To stay safe, you need to use every tool you have. Apple gives businesses many security features and frequent updates. These help protect iOS apps from cyber threats. Apple constantly works to improve security with new updates. This lets businesses stay ahead of risks.
A key part of Apple's security is app sandboxing. This keeps apps separate from each other and the system. If one app is breached, it can't spread to other apps. Apps are like vaults - each one is only accessed by itself. This greatly reduces the risk of data leaks or attacks across apps.
Code signing is a vital process that ensures apps are authentic and secure. All apps must have a digital certificate from Apple to prove they are safe and not tampered with. This certificate acts as a seal of approval, protecting users from harmful software.
Keeping software updated is crucial for security. Updates fix weaknesses and add new protections against hackers. Just like fortifying defenses against attacks, installing updates strengthens app security with the latest technology.
App sandboxing, code signing, and updating regularly create a trio of security measures. Businesses following these practices meet Apple's high standards and earn user trust. In today's digital world, earning trust is as vital as the services offered. Adopting these measures is essential for businesses to thrive.
The Importance of Privacy Policies and Compliance
Privacy policies and compliance are like navigating a maze. Each turn poses a challenge to data integrity and customer trust. They are not mere obligations but foundational elements protecting user data and building trust. According to Salesforce, 84% of consumers value data security highly when choosing whom to trust with their information. Clear and transparent privacy policies are paramount.
A privacy policy acts as a map for users. It shows how an app collects, stores, and uses data. This map builds trust by showing a commitment to privacy and security. Following rules like GDPR, HIPAA, and CCPA is like navigating by stars. These rules guide companies on properly handling and protecting data. They prevent companies from doing anything wrong with users' information.
Not following these rules can bring big problems. Companies face heavy fines for breaking privacy laws. In 2020, Twitter paid $550,000 for violating GDPR. But losing users' trust is an even bigger issue. It's very hard to regain trust once it's lost.
Privacy policies and following rules aren't one-time tasks. They continuously evolve as businesses grow and change. Companies must update their approach to match the ever-changing digital world. Only then can they remain guardians of user data.
Educating Your Team on Security Best Practices
In a business, each team member guards the security of apps. Their actions can strengthen or weaken cybersecurity defenses. Teaching security practices transforms team members. From potential risks, they become valuable assets. Learning cybersecurity turns them into a formidable force against threats.
A survey by CompTIA revealed that human error accounts for 52% of the root causes of security breaches. This startling statistic underscores the importance of comprehensive security training. By demystifying topics like robust password policies, the dangers of phishing scams, and the nuances of mobile device security, businesses empower their team to navigate the cyber landscape with confidence and caution.
Interactive workshops and regular training sessions can dramatically elevate the security consciousness within your team. For instance, simulated phishing exercises can sharpen their ability to spot and avoid malicious attempts to extract sensitive information. Such hands-on experiences reinforce theoretical knowledge, making the principles of cybersecurity resonate more deeply.
Furthermore, incorporating an understanding of the latest iOS security features and how to apply them can create a proactive culture of security. This knowledge enables developers and non-developers alike to recognize and report potential vulnerabilities, ensuring that security is woven into the fabric of your business operations from the ground up.
In this era of sophisticated digital threats, fortifying your team with the knowledge of security best practices is not merely educational—it's a critical layer of defense that enhances the overall security posture of your business applications. Engaging your team in this collective shield not only guards against external threats but also fosters a culture of vigilance and resilience that permeates every aspect of your digital endeavors.
Creating a Solid Plan to Handle Security Issues
In the digital world, cyber threats are constant dangers. Having a strong plan ready is crucial, not just smart - it's necessary. A robust incident response plan acts like a skilled team waiting to quickly respond to any security breach. This plan should clearly outline how to quickly identify, contain, and eliminate threats, as well as steps for recovery and analysis after the incident.
Research by IBM found that companies with a fully deployed incident response plan saved around $2 million compared to those without one. This shows that being prepared is financially wise. A good response plan isn't just about creating it, but also regularly testing and improving it. This way, when a breach happens, your team knows exactly how to respond.
The plan must also include communication strategies for notifying stakeholders and customers when needed. This maintains transparency and trust. In today's world, cyber incidents are inevitable. Having a ready incident response plan is key to protecting your digital assets and your company's reputation.
Real-Life Security Breaches: Lessons to Learn
Looking at past cybersecurity failures provides valuable warnings and shows us how to improve. For example, a major social media company suffered a breach in 2018 that exposed personal information of millions. This breach happened not just due to sophisticated hacking, but also vulnerabilities in the app's security itself. It emphasized the critical need for continually updating security measures and regularly checking for vulnerabilities. Even big tech companies are not safe from skilled cyber attackers.
Sometimes, we make mistakes that cause data leaks. A popular fitness app accidentally showed where military workers were moving. This showed how important privacy is when making apps. Small problems can have big effects around the world.
Breaches like these remind us that iOS apps face many threats. We need strong security measures. Technical defenses alone are not enough. We must also plan ahead to stop new threats. Learning from others' mistakes helps us build better defenses. With caution and care, we can stay secure in the digital world.
Upgrade your iOS app security with industry-standard solutions from the top iOS app development services in India. Safeguard valuable data and elevate your business today!
Conclusion
Securing iOS apps for businesses is not optional anymore. It is a must. The stakes are high. We risk financial loss, but more importantly, we risk losing customers' trust. We have many security tools: encryption, strong authentication, regular audits, secure coding, Apple's built-in features, and privacy policies. But the best tool is knowledge. We must understand threats and learn best practices. Cybersecurity threats keep changing, so we must keep learning and adapting too. Following security measures carefully protects our digital assets and reputation. In iOS app security, being watchful and proactive leads to lasting success.

 SURVEY
How Did You Hear About Us?
SURVEY
How Did You Hear About Us?




























Comments